Hello,
i want to build a separated vlan for wlan guests on three openwrt routers in my house. all the routers (2x Tl-WR1043ND v2, 1x WDR4300) are configured as switch with WLAN-AP, because the main router is a hardware firewall appliance.
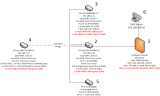
The physical network is addresses as 192.168.1.0/24, with 192.168.1.1 = firewall, 192.168.1.10/11/12 the openwrt devices.
Now i want to create a guest (w)lan (adressed e.g. with 192.168.100.0/24) with no access to the LAN, Internet only. I don't want any new cables, so vlan trunking should be the way to go.
I started with the OpenWRT device which is connected directly to the firewall over lan port 4. On the appliance i created a VLAN (ID 9) on the LAN-nic (Intel 82546GB [has 802.11q vlan support]).
now i am stuck, and very confused - after a lot of reading it has gotten worse, so i decided to ask here for help. What i have to do in OpenWRT, if port 4 is used by both the virtual and the physical network. Which one to tag, and how do i configure this in OpenWRT ?
Thanks a lot !