OpenWRT version: Chaos Calmer 15.05.1
Hardware: TL-WR1043ND v1.x
Flow: Carrier WAN Device >> OpenWRT >> LAN
Carrier device is attached to OpenWRT WAN interface with DHCP Enabled, set OpenWRT as DMZ.
Issue is that I am not able to remote connect from cloud to LAN devices (port forward used to work ok before I setup this, but it does not with Double NAT)
While I setup NAT (Masquerading) on Firewall zone, LAN is capable to connect to internet.
Case I remove it.. it does not reach internet. So I am using Double NAT at moment, but I would like to remove it.
I have allowed all connectivity between Zones in order to bypass this.. I will review once this is working.
WAN Device is managed.
root@OpenWrt:~# cat /etc/config/network
config interface 'loopback'
option ifname 'lo'
option proto 'static'
option ipaddr '127.0.0.1'
option netmask '255.0.0.0'
config globals 'globals'
option ula_prefix 'fd2f:a5e3:60d8::/48'
config interface 'lan'
option ifname 'eth0.1'
option force_link '1'
option type 'bridge'
option proto 'static'
option ipaddr '192.168.1.1'
option netmask '255.255.255.0'
option ip6assign '60'
config interface 'wan'
option ifname 'eth0.2'
option proto 'dhcp'
config interface 'wan6'
option ifname 'eth0.2'
option proto 'dhcpv6'
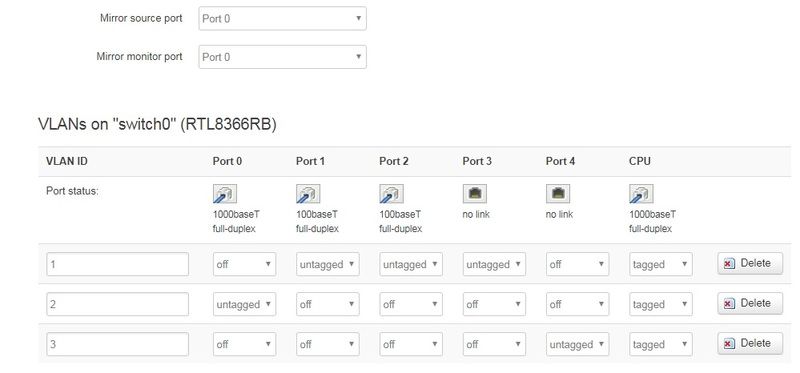
config switch
option name 'switch0'
option reset '1'
option enable_vlan '1'
config switch_vlan
option device 'switch0'
option vlan '1'
option ports '1 2 3 4 5t'
config switch_vlan
option device 'switch0'
option vlan '2'
option ports '0 5t'root@OpenWrt:~# cat /etc/config/firewall
config defaults
option syn_flood '1'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'REJECT'
config zone
option name 'lan'
option input 'ACCEPT'
option output 'ACCEPT'
option forward 'ACCEPT'
option network 'lan'
config zone
option name 'wan'
option output 'ACCEPT'
option input 'ACCEPT'
option forward 'ACCEPT'
option network 'wan wan6'
option masq '1'
option mtu_fix '1'
config rule
option name 'Allow-DHCP-Renew'
option src 'wan'
option proto 'udp'
option dest_port '68'
option target 'ACCEPT'
option family 'ipv4'
config rule
option name 'Allow-Ping'
option src 'wan'
option proto 'icmp'
option icmp_type 'echo-request'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-IGMP'
option src 'wan'
option proto 'igmp'
option family 'ipv4'
option target 'ACCEPT'
config rule
option name 'Allow-DHCPv6'
option src 'wan'
option proto 'udp'
option src_ip 'fe80::/10'
option src_port '547'
option dest_ip 'fe80::/10'
option dest_port '546'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-MLD'
option src 'wan'
option proto 'icmp'
option src_ip 'fe80::/10'
list icmp_type '130/0'
list icmp_type '131/0'
list icmp_type '132/0'
list icmp_type '143/0'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Input'
option src 'wan'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
list icmp_type 'router-solicitation'
list icmp_type 'neighbour-solicitation'
list icmp_type 'router-advertisement'
list icmp_type 'neighbour-advertisement'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config rule
option name 'Allow-ICMPv6-Forward'
option src 'wan'
option dest '*'
option proto 'icmp'
list icmp_type 'echo-request'
list icmp_type 'echo-reply'
list icmp_type 'destination-unreachable'
list icmp_type 'packet-too-big'
list icmp_type 'time-exceeded'
list icmp_type 'bad-header'
list icmp_type 'unknown-header-type'
option limit '1000/sec'
option family 'ipv6'
option target 'ACCEPT'
config include
option path '/etc/firewall.user'
config rule
option src 'wan'
option dest 'lan'
option proto 'esp'
option target 'ACCEPT'
config rule
option src 'wan'
option dest 'lan'
option dest_port '500'
option proto 'udp'
option target 'ACCEPT'
config redirect
option target 'DNAT'
option src 'wan'
option dest 'lan'
option proto 'tcp'
option src_dport '444'
option name 'Escritorio'
option dest_ip '192.168.1.10'
option dest_port '555'
config forwarding
option dest 'lan'
option src 'wan'
config forwarding
option dest 'wan'
option src 'lan'root@OpenWrt:~# route -n
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
0.0.0.0 192.168.15.1 0.0.0.0 UG 0 0 0 eth0.2
192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 br-lan
192.168.15.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0.2
192.168.15.1 0.0.0.0 255.255.255.255 UH 0 0 0 eth0.2(Last edited by zetto33 on 5 Sep 2017, 09:40)